Memorandum
Subject: The China Problem
To: All Readers and Interested Parties
From: Greg Smith, Author
Date: 21 October 2025
BACKGROUND:
Throughout the Cold War, both the US and the Union of Soviet Socialist Republics (USSR) competed for global influence. Most of the competition was through diplomatic, economic and other indirect methods. Espionage was rampant on both sides, as each sought to find and gain advantage. Neither was willing to engage in direct military confrontation due to the risk of escalation into nuclear warfare. However, both engaged in military entanglements through proxies and third-party players. Both also leveraged allies in these entanglements.
For most of the latter half of the twentieth century, China was a side note and minor player. Mao Zedung and his communist followers completely took over the Chinese mainland in 1949, proclaiming the People’s Republic of China on October 1, 1949. The competing Nationalist Chinese, under Chiang Kai Shek retreated to the island of Taiwan, forming the Republic of China. Communist China does not recognize Taiwanese independence and continues to claim the island as part of greater China. Taiwan remains independent and friendly to the US.
When communist North Korea invaded South Korea in 1950, the US and UN allies feared the conflict would precipitate additional communist takeovers. The prevailing theory was that nations would fall like dominoes across Asia if Korea succumbed to communist takeover. This idea became known as the “Domino Theory,” and dominated US policy for decades. The US intervened in Korea and looked to have the upper hand until China sent hundreds of thousands of troops south to fight against the “imperialist west.” The Chinese intervention was buttressed by their Soviet allies, who saw the opportunity for expanded influence in Asia. The war ended in a stalemate after three years of fighting, and a peace deal segmented the Korean Peninsula at the 38th parallel. The armistice is still in place, cementing the division of North (communist) and South Korea.
After the Korean War, China became more isolated on the world stage. Initially, China and the USSR remained close allies. However, China sought more independence and influence around the world. Mao initiated several collectivization programs under the “Great Leap Forward.” In 1960, the growing ideological rift with the USSR resulted in the expulsion of Soviet economic advisors from China. China pressed on, developing a nuclear program that culminated with a successful device in 1964.
 In 1966, Mao initiated a “New Cultural Revolution” that lasted through his death ten years later. The effort was a political and social program to reinvigorate the spirit of the 1949 rebellion and cement Mao’s legacy and power. The new programs were also aimed at helping China become more important globally and signaled a willingness to open the door to new diplomatic ties with the west.
In 1966, Mao initiated a “New Cultural Revolution” that lasted through his death ten years later. The effort was a political and social program to reinvigorate the spirit of the 1949 rebellion and cement Mao’s legacy and power. The new programs were also aimed at helping China become more important globally and signaled a willingness to open the door to new diplomatic ties with the west.
In 1972, President Richard Nixon famously visited Communist China. At the time it was considered a tremendous accomplishment and hailed as the great reopening of China. Nixon may have had ulterior motives to distract from the Watergate scandals or to move past the Vietnam experience, but the visit was largely portrayed as a success to open trade. Diplomatically, it was also a slap at the USSR, China’s former benefactor and key ally. Businesses flooded into the untapped market of one billion people. It was not long before China saw opportunity and quickly became the cheaper manufacturing alternative for Western countries.
Industrialists, companies, and investors flocked to China for cheap labor, high margins and low-cost manufacturing. Westerners became rich through high margins and favorable trade terms, encouraging even more outsourcing to Chinese firms. The Chinese Communist Party (CCP or Party) profited along with the hand-selected, politically aligned Chinese entrepreneurs. The era of western outsourcing and offshoring followed, as more firms moved facilities and manufacturing capability to China, India, Mexico and other nations. Plants and businesses that failed to offshore to Chinese firms faltered, failed or were swallowed up by thriving competitors. China encouraged the expansion and kept costs low enough to entice businesses. America, once the manufacturing hub of the world, was supplanted by China and other states as manufacturing capability collapsed.
While China, and the CCP, reaped huge economic rewards, they were also looking for advantages. China became a master at reverse-engineering products and creating lower-cost imitations of both low and high technology products. As the global demand and consumption of technology expanded, China ensured a place at the table through cheap labor, enormous manufacturing capability and low costs. Thanks to low costs, high margins and extensive manufacturing capability, China has successfully taken control over a wide range of manufacturing, including ship building, electronics, steel, and Rare Earth Elements (REE) and magnets.
China has always had a long-term strategy to become the dominant world power, both economically and militarily. Within a few years of Nixon’s visit, China began sending hand-picked students, businesspeople, investors, and scientists to the West for advanced training and education. Chinese students and business flowed into universities, along with large dollar donations, endowments and other incentives. The seed was planted, and it flourished.
Universities, businesses, and governments sought partnerships with Chinese firms and research facilities. Chinese officials said yes to medical, biological, technological, and any other research request. Like the manufacturing facilities, China accepted lower standards for quality and safety than would not be allowed or tolerated in most Western countries. China has also reportedly allowed the use of slave labor for mining and other dangerous work to support the industrialization efforts. As a result of the willingness to take on all work, western countries opened the door for exploitation and have exposed themselves to serious national security issues.
INTELLIGENCE ASSESSMENTS:
Evaluating Chinese intent and activity is never a straightforward endeavor. Since the “opening” of China by Nixon in 1972, China has sought to enhance their image, grow their influence, and become the dominant global superpower. China recognized that they were forty years or more behind the West and even the Soviets and lacked the infrastructure necessary to resolve that gap. China resulted to subterfuge, espionage, economic coercion, and blatant theft to overcome their deficiencies.
When assessing Chinese actions, it is important to remain grounded on Chinese philosophy concerning war and competition, which can be stated through the works of Sun Tzu (544 – 496 BCE). In his seminal work, The Art of War, he postulates that “To subdue the enemy without fighting is the acme of skill.” A second saying often attributed to the writer states “Wait by the river long enough, and the bodies of your enemies will float by.” These sayings, when taken together, help explain the extensive use of espionage of all types, coercion, and economic manipulation by China.
Understanding Chinese tactics requires understanding the absolute control over the nation by the CCP. In China, people are not allowed to travel freely, create businesses, conduct scientific research, and negotiate contracts without the consent of the party. Even the criminal element in China cooperates actively with the CCP and is used for illegal activity in other countries for the benefit of the Party. Understanding that all activity related to China or Chinese citizens is likely tied to a greater or lesser degree to CCP desires.
China makes extensive use of their economic position to finance their global aspirations. After years of encouraging foreign investment into their economy, China now holds a dominant position in many manufacturing sectors. Foreign investments into China fueled a massive expansion, while their mastery of reverse-engineering products helped China to build their skill base. Further, western firms eagerly signed non-disclosure and similar agreements with Chinese firms expecting a level of secrecy not rationally available in China. Western firms fund their own competition and are unable to effectively sue their Chinese counterparts when duplicates and replicas of western products flood the market at lower prices.
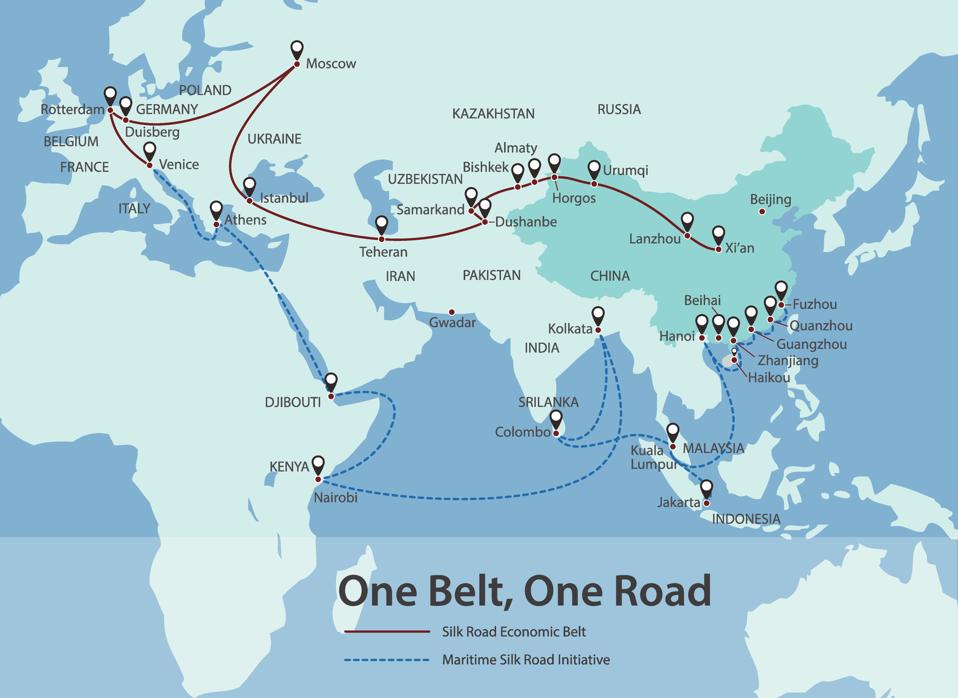
 China also uses economic coercion to spread their influence around the world. In the “Belt and Road Initiative,” China provided low interest loans to countries in Asia, Africa, and even Europe for infrastructure projects. Chinese officials and businesspeople convinced governments to take on massive loans and build infrastructure projects on the vague promise that economic activity would follow. China financed new airports, railroads, bridges, and roads, and seaports. Most of those new projects either were never completed or resulted in tremendous debt to the gaining country. Massive new and modern seaports, airports and railways sit idle because the market was never there for such projects.
China also uses economic coercion to spread their influence around the world. In the “Belt and Road Initiative,” China provided low interest loans to countries in Asia, Africa, and even Europe for infrastructure projects. Chinese officials and businesspeople convinced governments to take on massive loans and build infrastructure projects on the vague promise that economic activity would follow. China financed new airports, railroads, bridges, and roads, and seaports. Most of those new projects either were never completed or resulted in tremendous debt to the gaining country. Massive new and modern seaports, airports and railways sit idle because the market was never there for such projects.
 Economically, these projects were disasters for countries like Sri Lanka, Tanzania, Malaya, Kenya and Pakistan. The projects ensnarled the countries in overwhelming debt which enabled China to swoop in to take over the facilities with 99-year operating agreements. Economically, the projects were a disaster, but in the end, China gains global leverage. China controls and operates a global logistics infrastructure they built using other countries money.
Economically, these projects were disasters for countries like Sri Lanka, Tanzania, Malaya, Kenya and Pakistan. The projects ensnarled the countries in overwhelming debt which enabled China to swoop in to take over the facilities with 99-year operating agreements. Economically, the projects were a disaster, but in the end, China gains global leverage. China controls and operates a global logistics infrastructure they built using other countries money.
When duplicates are not required or feasible, China installs back-doors and hidden control features in western technology. Examples of this include the expansion of “green technology” products produced in China. China eagerly supports global initiatives to reduce emissions from coal and fossil fuels while simultaneously establishing new coal fired power plants at the rate of one per week. China developed an extensive manufacturing capability for “green technology” like solar panels and batteries. China recognized that western powers were willing to openly sacrifice their power systems to new technology and would need massive numbers of renewable energy products, while their own closed society enabled plausible deniability of their hypocrisy.
EV battery technology is expensive to produce and requires minerals that are either mined in China or provided by Chinese partners. Also, China leveraged the desire of western automakers to reach the large Chinese market with EVs. Within a few years of establishing manufacturing and sales channels in China, new Chinese-made EVs began appearing on the market. Naturally, the Chinese EVs are priced significantly lower than the competition and often produced with inferior quality controls. The Chinese EV brand BYD is now the largest producer of EVs in the world and sells them in most markets (except the US).
Like other Chinese technology, Chinese EVs come with risks. Chinese EVs flooded the Australian market and were lauded by political figures as a way to reach net-zero goals. The Home Affairs Minister and other political figures purchased Chinese EVs for personal use. In 2024 and 2025, Chinese EVs were found to have remote kill switches, microphones, cameras, and sensors that could be controlled remotely. Australian Cybersecurity experts warned government officials to not have conversations while riding in Chinese made cars. Still, China is pushing to become the dominant EV auto maker, through both product dumping (at low cost) and acquisition of competitors. China now owns or holds large portions of Volvo, Polestar, MG, and Lotus, all of which are heavily involved in EV production.
 Other green tech has also been exploited by China. In 2025, thousands of Chinese-made solar panels in the US, Europe and the UK were discovered to have hidden kill switches installed. Rogue communication devices were also discovered in solar inverters. These devices could theoretically communicate with China directly and enable Chinese operatives to control the power grid where these devices were installed, or to infect the power companies with viruses or other hacks to either control power supplies or steal user information. Thanks to low costs, China is the dominant producer of solar panels, inverters and other green power products.
Other green tech has also been exploited by China. In 2025, thousands of Chinese-made solar panels in the US, Europe and the UK were discovered to have hidden kill switches installed. Rogue communication devices were also discovered in solar inverters. These devices could theoretically communicate with China directly and enable Chinese operatives to control the power grid where these devices were installed, or to infect the power companies with viruses or other hacks to either control power supplies or steal user information. Thanks to low costs, China is the dominant producer of solar panels, inverters and other green power products.
China is also a dominant producer of consumer technology. Chips, memory modules, hard drives, cameras, microphones, and internet hardware are all largely produced in China. Even those items not produced in China may contain Chinese made parts. In the mid-2000’s, the US Government (USG) issued a notification concerning the use of Huawei video cameras and other devices containing parts from the Chinese manufacturer. At the time, several USG departments were found to have vulnerable devices in their facilities. The devices on the banned list include cameras, smart watches, speakers, and other products.
More recently, the concern over REE and magnets has gained wider attention in the US press. REEs are a group of seventeen elements usually found in trace amounts, like scandium and lithium, that have unique magnetic, catalytic, or luminescent qualities useful in high technology applications. REE must be mined and processed in great amounts. From the 1960’s through the 1980’s, the US was the dominant producer of REE globally. The rise in technology dependence in the west, combined with increased environmental concerns caused a rapid reduction in REE production in the US. Although the US has up to twenty times the reserves of REE as China, according to the US Geologic Survey (USGS), mining and processing capacity has dwindled. China overtook the US in REE production in the 1990s and now controls 70-90% of the global supply chain. REE are critical for both consumer and military applications, communications systems, and EV battery technology.
 Chinese-backed crime also threatens the west. The USG estimates that between 2021 and 2024, Chinese hackers laundered more than $4 billion of funds stolen through cyber hacking and fraud. Chinese cybercrime and espionage alone accounts for approximately 2.4 million attempts daily. The CCP is known to leverage criminal gangs to intimidate and control dissidents and Chinese citizens residing abroad. Chinese crime gangs infiltrate protest organizations, Chinese cultural societies, drug trafficking and even human trafficking activity. China is the largest producer for fentanyl precursors and ships large quantities to criminal gangs in Central and South America as well as Europe.
Chinese-backed crime also threatens the west. The USG estimates that between 2021 and 2024, Chinese hackers laundered more than $4 billion of funds stolen through cyber hacking and fraud. Chinese cybercrime and espionage alone accounts for approximately 2.4 million attempts daily. The CCP is known to leverage criminal gangs to intimidate and control dissidents and Chinese citizens residing abroad. Chinese crime gangs infiltrate protest organizations, Chinese cultural societies, drug trafficking and even human trafficking activity. China is the largest producer for fentanyl precursors and ships large quantities to criminal gangs in Central and South America as well as Europe.
https://tinyurl.com/ChinaEspionage
https://tinyurl.com/Techvulnerability
https://tinyurl.com/ChinaCyberView
https://tinyurl.com/REEcapacity
https://tinyurl.com/SSScommnet
Although most people consider Russia, Iran, or various affiliated terror groups to be the top threat to the US, a case can be made that China is the greater threat. Chinese intrusion into key infrastructure, such as the power grid, constitutes a potential vulnerability to future exploitation. In the event of a direct conflict or increased tensions with China, the west stands open to attack.
During the run-up to the United Nations Global Summit in September, authorities discovered an illicit communications network just blocks from the UN building in Manhattan. The facility included dozens of servers and 100,000 cellular sim cards. The facility was designed to operate remotely and could generate enough simultaneous cellular traffic to completely overwhelm established networks. Such capability, if combined with physical attacks, would effectively deny communications to emergency services, first responders, and civilians in need of help.
Although the illicit communications facility in New York has not been formally attributed to China, unconfirmed reports in the press point to China as the likely culprit. The configuration, capacity and financing required clearly point to a state-level actor. A second facility with twice the capacity was uncovered in New Jersey just days later. Hopefully, the search for similar targets is ongoing in Washington, D.C. and other major cities across the US.
October is cyber awareness month. Look at how much of your home and personal life includes technology or equipment built in China, one of their allied states, or uses Chinese parts. It is likely that you interact with Chinese technology daily in ways that you never even thought about.
CURRENT OPERATIONS UPDATE:
I had a great discussion with my Story Editor for Killer’s Reign, and she provided excellent feedback and suggestions. I am making several revisions, additions and changes to prepare the story for another round of edits and then publication. The changes make the story stronger, more entertaining and a much better read. I plan to complete the manuscript in the next few weeks. Meanwhile, I continue to work the rewrite of Sleeper Cell and develop the plot and story line for a World War II historical fiction thriller and associated screenplay.
COMMUNICATIONS UPDATE:
All my stories are passion projects and stories I enjoy reading as well as writing. I also write some nonfiction, including the recently released The Coach’s Playbook, which was a collaboration project that became a best-seller on Amazon in July. I recently submitted a section for inclusion to The Success Playbook, which will be released in February, 2026.
My fiction stories, Killer’s Reign and Sleeper Cell draw heavily on current events. Although works of fiction, I strive to ensure that the events and characters are plausible and representative of real word events and scenarios.
Check my website regularly for more information about my books and stories, updates on current events, and interesting tidbits of intelligence.
Stay safe, stay alert, stay informed.
Greg Smith
Author
cc:
S2 Intelligence
S3/5 Operations & Plans
S6 Communications





